Switches are used to connect multiple devices on the same network within a building or campus. For example, a switch can connect your computers, printers, and servers, creating a network of shared resources. The switch, one aspect of your networking basics, would serve as a controller, allowing the various devices to share information and talk to each other. Through information sharing and resource allocation, switches save you money and increase productivity.
Routers, the second valuable component of your networking basics, are used to tie multiple networks together. For example, you would use a router to connect your networked computers to the Internet and thereby share an Internet connection among many users. The router will act as a dispatcher, choosing the best route for your information to travel so that you receive it quickly.
To enrich your career and become a VMware professional, visit Tekslate, the global online training platform:" VMware Training". This course will help you achieve excellence in this field.
Routers analyze the data being sent over a network, change how it is packaged, and send it to another network, or over a different type of network. They connect your business to the outside world, protect your information from security threats, and can even decide which computers get priority over others.
Depending on your business and your networking plans, you can choose from routers that include different capabilities. These can include networking basics such as:
Firewall: Specialized software that examines incoming data and protects your business network against attacks.
Virtual Private Network (VPN): A way to allow remote employees to safely access your network remotely.
IP Phone network: Combine your company's computer and telephone network, using voice and conferencing technology, to simplify and unify your communications.
VMware Virtual Networking Concepts:
A virtual network provides networking for hosts and virtual machines that use virtual switches.
Virtual switches allow virtual machines on the same ESX Server host to communicate with each other using the same protocols that would be used over physical switches, without the need for additional networking hardware. ESX Server virtual switches also support VLANs that are compatible with standard VLAN implementations from other vendors.
A virtual machine can be configured with one or more virtual Ethernet adapters, each of which each has its own IP address and MAC address. As a result, virtual machines have the same properties as physical machines from a networking standpoint. In addition, virtual networks enable functionality not possible with physical networks today.
Models a physical Ethernet switch:
-A virtual machine’s NIC can connect to a port.
-Each uplink adapter uses one port.
A virtual switch allows the following Two types of connection:
VMkernel port group: This Port is used to handle the services traffic.
-For example, for IP storage or vMotion migration
-For the ESXi management network
Virtual Machine port group: This port is used to handle all the virtual machines incoming and outgoing traffic to the physical Networks.
Virtual Machine and VMkernel port groups are connected to the external world through a Physical Ethernet adapter that is connected to the virtual switch uplink port.
A virtual network supports two types of virtual switches:
vNetwork standard switches:
Virtual switch configuration for a single host.
vNetwork distributed switches:
Virtual switches that provide a consistent network configuration for virtual machines as they migrate across multiple hosts.
vNetwork standard switches can have Maximum 4088 virtual switch ports per Standard Switch and 4096 virtual switch ports per host.
VLANs
VLANs provide for logical groupings of stations or switch ports, allowing communications as if all stations or ports were on the same physical LAN segment. Confining broadcast traffic to a subset of the switch ports or end-users saves significant amounts of network bandwidth and processor time. There are several benefits of using VLAN include the following :
-Create logically grouped Networks.
-Improve Performance by confining broadcast traffic to a subnet of the switch port.
-Save the cost by portioning the network without the overhead of routers.
ESXi supports 802.1Q VLAN tagging.
Virtual switch tagging is one of three tagging policies supported.
-Packets from a virtual machine are tagged as they exit the virtual switch.
-Packets are untagged as they return to the virtual machine.
-Affect on performance is minimal.
ESXi provides VLAN support by giving a port group a VLAN ID
Physical Network Considerations:
Discuss VMware vSphere® networking needs with your network administration team. Discuss the following issues:
-Number of physical switches
-Network bandwidth required
-Physical switch support for 802.3AD (for NIC teaming)
-Physical switch support for 802.1Q (for VLAN trunking)
-Network port-security
-Cisco Discovery Protocol (CDP) and its operational modes: listen, broadcast, listen and broadcast, and disabled.
How to create a vStandard Switch?


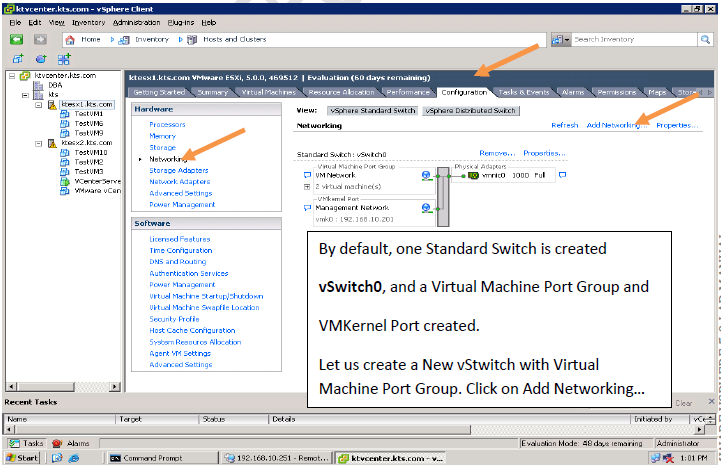





















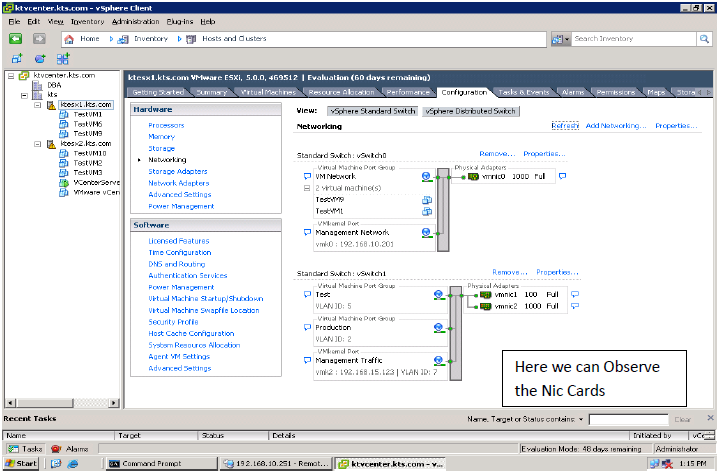
Networking Policies:
Three network policies:
Security
Traffic shaping
NIC teaming
Policies are defined:
At the standard virtual switch level:
-Default policies for all the ports on the standard virtual switch
At the port or port group level:
-Effective policies: Policies defined at this level override the default policies set at the standard virtual switch level
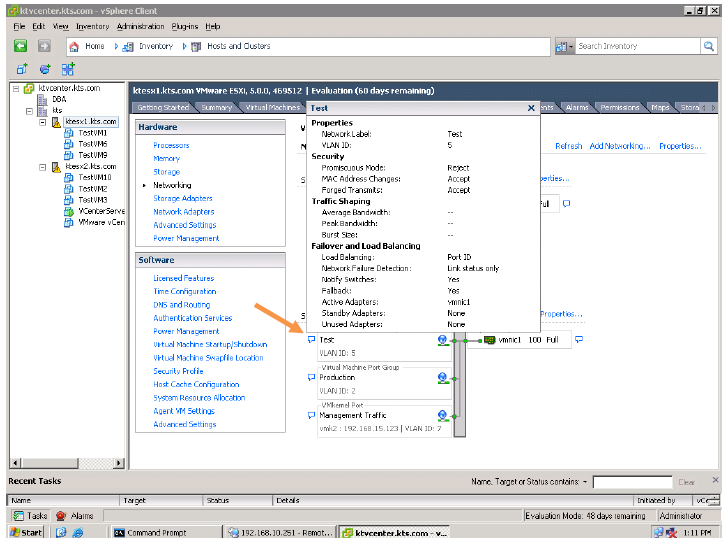
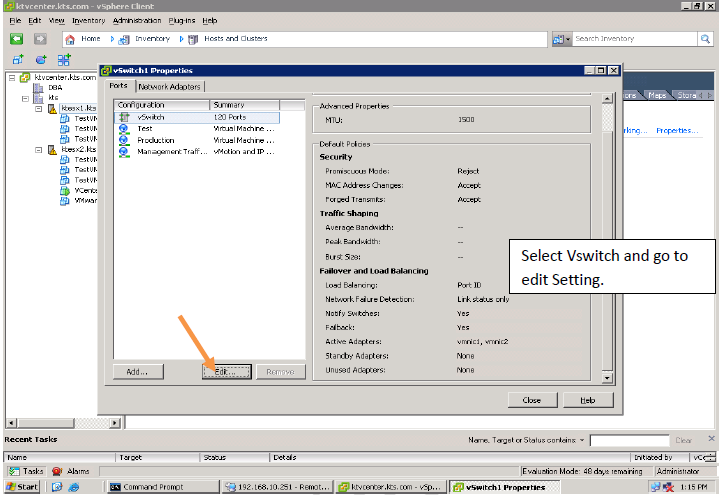
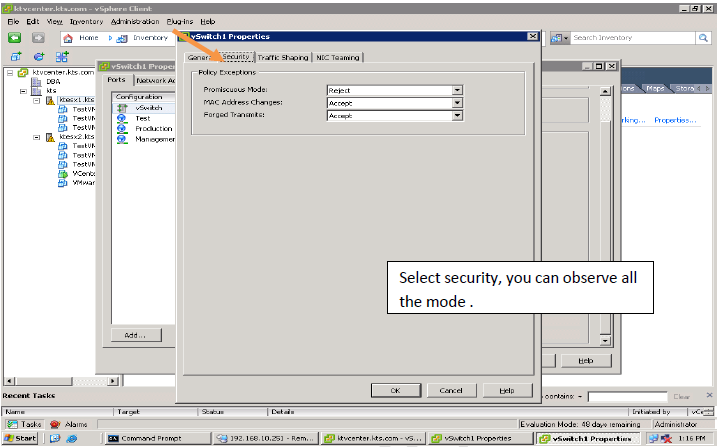
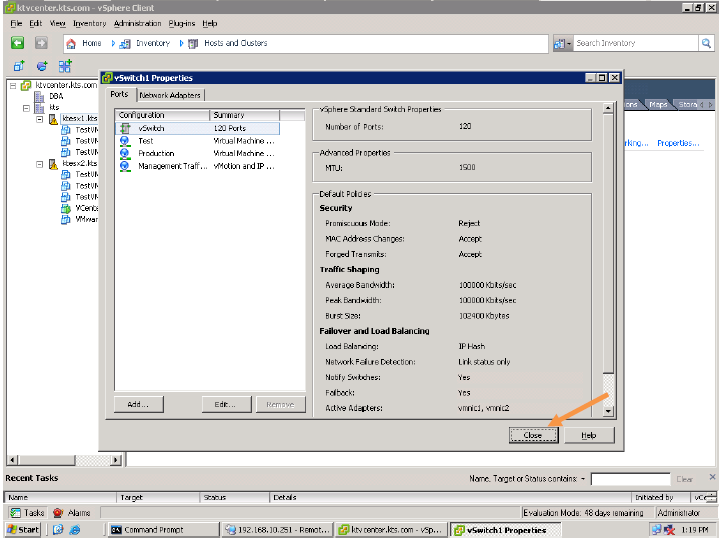
Security Policy:
Administrators can configure layer 2 Ethernet security options at the standard virtual switch and at the port groups.
Three Security Policies :
Promiscuous mode: By default this Reject, This is used for troubling shooting purpose.
MAC Address: By default this Accept, This is used to handle the Incoming Traffic or Packets
Forged Transmit: By default, this is Accept, This is used to handle the outgoing Traffic or Packet.
Traffic-Shaping Policy :
Network traffic shaping is a mechanism for controlling a virtual machine’s network bandwidth.
Three Traffic-shaping Policy: Average rate, peak rate, and burst size are configurable.
Note: Thee traffic shaping policies are configured with the advice of Network Admin.
Traffic shaping is disabled by default.
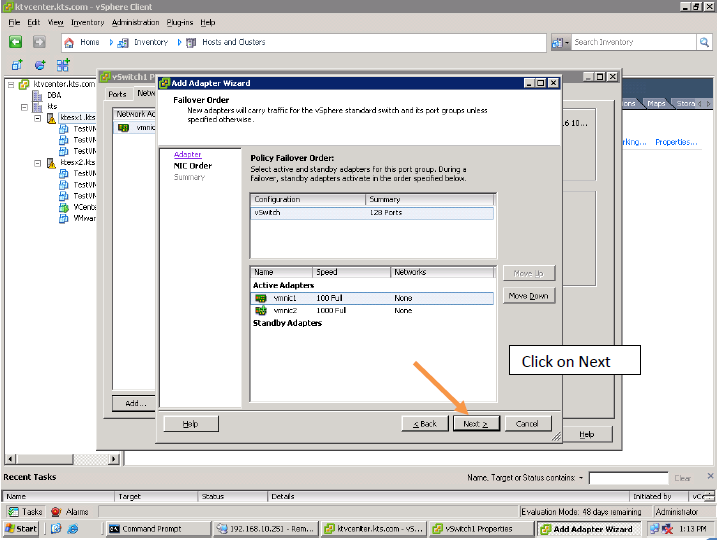
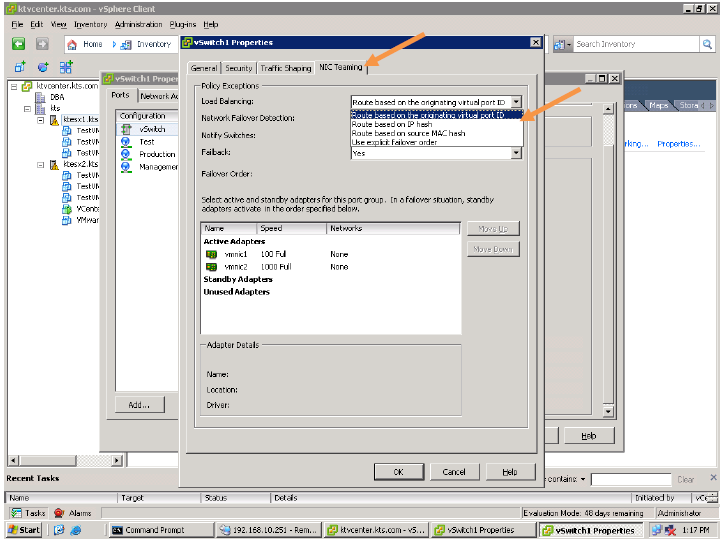
NIC Teaming Policy:
Load Balancing (outbound only)
Network Failure Detection
Notify Switches
Failback
Failover Order
Load Balancing Policies are :
Load-Balancing Method: Originating Port ID
Load-Balancing Method: Source MAC Hash
Load-Balancing Method: IP-Hash
Note: The Best Load Balancing Policy is IP-Hash.
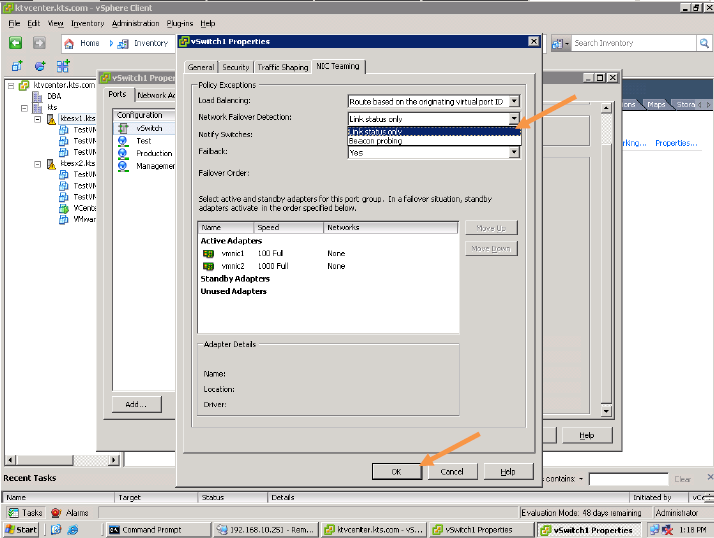
Detecting and Handling Network Failure
Network failure is detected by the VMkernel, which monitors:
Link state only
Link state plus beaconing
Switches can be notified whenever:
There is a failover event
A new virtual NIC is connected to the virtual switch
Failover implemented by the VMkernel based on configurable parameters:
Failback: How a physical adapter is returned to active duty after recovering from a failure
Load-balancing option: Use explicit failover order. Always use the highest order uplink from the list of active adapters that pass failover detection criteria.









For an in-depth understanding of VMware:
You liked the article?
Like: 0
Vote for difficulty
Current difficulty (Avg): Medium

TekSlate is the best online training provider in delivering world-class IT skills to individuals and corporates from all parts of the globe. We are proven experts in accumulating every need of an IT skills upgrade aspirant and have delivered excellent services. We aim to bring you all the essentials to learn and master new technologies in the market with our articles, blogs, and videos. Build your career success with us, enhancing most in-demand skills in the market.